Cyber Risk Trends: 10 Threats to Watch Out For
January 18, 2021
2020 was a record year for cyberattacks. The global health crisis, combined with a distracted workforce, overwhelmed IT teams, and economic upheaval, has effectively catapulted the world into a new age of cyber threat. 80% of Canadian organizations have reported experiencing at least one cyberattack that impacted their databases last year; 21% have faced more than 10 attacks.


2020 was a record year for cyberattacks. The global health crisis, combined with a distracted workforce, overwhelmed IT teams, and economic upheaval, has effectively catapulted the world into a new age of cyber threat. 80% of Canadian organizations have reported experiencing at least one cyberattack that impacted their databases last year; 21% have faced more than 10 attacks.
Businesses are combatting COVID-19 on multiple fronts; new challenges posed by the pandemic itself are accompanied by the heightened risk of cybercrime. Companies are relying on digital solutions to make it through—email, cloud services, online forms, and more—but these very technologies simultaneously boost their vulnerability to attack. Hackers have been shameless in their attempts to exploit public concern and fears, with remote workers, SMBs, and healthcare organizations disproportionately targeted.
From financial aid scams to fake apps to ransomware events, we’ve seen a myriad of tactics employed by cybercriminals throughout the year. Threats are evolving faster than ever and the sheer volume of attacks is taking its toll on cyber insurance providers, who may be looking to pull back on coverage.
What will the cyber landscape look like in 2021? What are the emerging risks? How can businesses prepare for the challenges that lie ahead? To answer these questions, let’s delve into the biggest cyber vulnerabilities of 2020 and upcoming trends for the new year. In this piece, we’ll go over the most popular methods of attack, top uses for stolen data, and leading risks posed by digital response measures—and what businesses can do to minimize their exposures.
Disclaimer: Please note that the information provided herein offers guidelines only. It is not exhaustive and does not constitute legal, insurance, or cybersecurity advice. For more guidance, please consult a lawyer, a licensed insurance representative, and/or a cybersecurity specialist.
What were the most popular methods of attack?
COVID-19 has rapidly exacerbated the barrage of cyber and technology risks businesses, consumers, and public institutions already contend with on a daily basis. 31% of companies around the world have been targeted by a cyberattack at least once a day throughout the pandemic. Attackers have pivoted to take advantage of mass teleworking, employees’ heightened state of vulnerability, and the online shopping boom.
Historically, most attacks have been aimed at large enterprises with pockets deep enough to pay ransom demands, recover data, or swallow a loss. However, large companies could also afford to thicken their security layer and avoid future attacks.
Consequently, cybercriminals have directed their attention to SMBs with limited defences and budget. Research from Keeper Security even shows that about half of private-sector SMBs spend less than $5,000 per year on cybersecurity, leaving a huge gap for criminals to wreak havoc.
Phishing Attacks by Country (Global %)
Global Ransomware Damages (Billions $)
DDoS Average Cost of Business Interruption
Phishing Attacks by Country (Global %)
Global Ransomware Damages (Billions $)
DDoS Average Cost of Business Interruption
Phishing
A classic cybercriminal maneuver, phishing is a type of social engineering scam wherein attackers try to trick, coax, or “phish” people into disclosing private information by clicking on bogus links, opening infected attachments, or downloading malware.
By far and away, phishing was the most popular method of attack for threat actors throughout 2020. A report from RSA names Canada as the most frequently targeted country for phishing scams in Q1 2020, accounting for 66% of global attacks. In comparison, the US, which placed second overall, only received 7%.
Fraud centres worldwide have reported thousands of coronavirus-related phishing campaigns, or “scareware,” as workers’ reliance on email and the Internet has increased. And while the emails of yesteryear were riddled with grammatical errors, typos, and breaks in text, the scams of today have become much more sophisticated, convincing, and seemingly legitimate.
Common scams include urgent, threatening, or foreboding messages that:
-
Offer PPE, medical supplies (both natural and pharmaceutical), or government aid;
-
Seek donations for fraudulent charities, relief funds, and/or research;
-
Impersonate trusted government or public health agencies to deliver urgent news about COVID-19 or sell products that claim to prevent, diagnose, or treat the virus;
-
Impersonate high-ranking executives from the victim’s company (like the President or CEO) and demand immediate action (confirming financial details or payroll information);
-
Invite users to fake Zoom, Skype, or video meetings and request login credentials;
-
And more. A full list can be found here.
Ransomware
The number one cyber claim in Canada in 2020 was ransomware, in which attackers lock or encrypt data and threaten to release it unless a ransom is paid within a set amount of time. The first quarter of 2020 saw a 25% jump in attacks from Q4 in 2019, with new events occurring every 14 seconds. Between January and June, the ID Ransomware database recorded over 100,000 incidents aimed at companies and public sector organizations.
Generally speaking, ransomware attacks target organizations that either have access to confidential data, greater dependence on technology, or weak security; in short, companies that seem likelier to pay up. And unlike most attacks, where criminals must first steal information, and then find willing buyers, ransomware paydays are more or less immediate since most organizations can’t function without their data.
Following the outbreak of coronavirus, cybercriminals have ramped up their efforts against:
-
Supply Chains: Supply-chain style attacks seek to compromise a larger network by gaining entry through a less secure outside partner, provider, or other third-party. For attackers, smaller, resource-poor companies, like distributors, suppliers, and vendors, are low-hanging fruit that might potentially open the door to bigger enterprises or multinational corporations. Manufacturing businesses, in particular, took a big hit in Q1, with a 156% rise over the previous quarter.
-
Healthcare Agencies: 29% of ransomware events target healthcare organizations, with the most successful attacks hitting facilities with fewer than 500 employees. Why? Quite simply, the loss of critical patient data and extended downtime can jeopardize human lives—especially in the middle of a global pandemic—making it near impossible for victims to refuse or delay payment. Notable Canadian victims include: Vancouver Coastal Health in May, the BC Cancer Foundation in July, and the Medisys Health Group in August, who had to pay up to recover the stolen data of some 60,000 clients.
DDoS Attacks
In a distributed denial of service (DDoS) attack, a threat actor floods the bandwidth of a web-based system with hundreds of dummy connections to overload the servers. Networks are bogged down with traffic, leaving victims unable to access saved files or deliver services, while the hackers make off with valuable information.
Attacks are easy to launch and don’t last long—about ten minutes or less—but the cost of business interruption is high. Experts estimate that downtime costs businesses $350,000 an hour on average. That means even a five-minute attack could cost a company $30,000.
DDoS attacks are routinely directed towards cloud software and VPN servers, which, if compromised, can put entire workforces offline. Naturally, with the widespread adoption of both in businesses across all industries last year, DDoS attacks have surged in intensity, sophistication, and volume. Neustar’s Cyber Threats & Trends Report saw a 151% increase in the number of attacks between January and June 2020 compared to the same period in 2019. That figure also includes the longest attack Neustar has ever seen at 5 days and 18 hours.
As lockdowns have taken hold, gaming, media, retail and e-commerce, and healthcare organizations have been among the most affected. This is largely due to growths in revenue and/or traffic attributed to the pandemic—and where traffic rises, so too do attacks.
Formjacking
Formjacking, also known as e-skimming, is an attack method that uses malicious JavaScript code to retrieve user data from online pages. It’s generally used on websites’ checkout pages to siphon credit card numbers, banking details, addresses, and more. Attacks are almost impossible to detect; transactions go through as normal and the user will still receive their products, but they won’t know their information has been stolen until they check their accounts.
Due to the rising popularity of online retailers and online shopping, formjacking has quickly become one of the fast-growing methods of cyberattack. In 2019, Symantec reported an average of 4,800 websites per month that were compromised by formjacking code.
Then the pandemic hit. To prevent virus transmission, organizations large and small turned to digital payment forms to enable online purchases, curbside pickup, and virtual services while their brick-and-mortar locations were closed or at limited capacity. And with more people at home than ever before, online shopping has reached levels previously unseen, followed by a commensurate rise in formjacking. A whopping $434.5 billion was spent on online purchases in the first seven months of 2020, including an extra $94 billion driven by COVID-19 since March. At the same time, Q1 2020 saw 7,836 websites compromised by formjacking.
One of the biggest hacks last year? Fitness Depot. A timely attack, considering online sales of fitness equipment shot up 55% between January and March 2020 with gyms and fitness centres closed.
What were the top uses for stolen data?
Phishing, DDoS, and formjacking are usually gateways to other forms of attack or extortion. Most of the time, information stolen in large-scale data breaches is either stockpiled for future use or sold on the Dark Web to be leveraged in credential stuffing attacks and identity theft.
Credential Stuffing
Credential stuffing is a type of cyberattack that uses login credentials from a prior data breach (user IDs, email addresses, passwords, and/or pin numbers) to gain unauthorized entry to other accounts. If an attacker successfully infiltrates an employee or admin account, they’ll find more than just business contacts or clients’ addresses; they might also access classified corporate data, like intellectual property, trade secrets, or payroll information.
Much like DDoS and formjacking, credential stuffing has skyrocketed due to the rise of COVID-scams and e-commerce. During the lockdowns in Q1, cybercriminals collected and circulated dozens of password combination lists on the Dark Web to identify vulnerable accounts, which were hijacked amid the online shopping boom of Q2-4. Findings from Arkose Labs reveal 1.3 billion fraud attacks from Q3 alone, with 770 million of them employing credential stuffing.
What makes credential stuffing so effective? Users are committing cardinal sins of password creation and use, such as: password sharing, weak passwords, lack of multifactor authentication, and more. And because people often reuse the same username and password across various platforms, personal and professional, a single set of credentials can be used to unlock multiple accounts.
Personal Identity Theft
In addition to draining bank accounts and credit cards, hackers are using personal information obtained in data breaches, phishing, DDoS, formjacking, and credential stuffing attacks to capitalize on new opportunities presented by the pandemic, such as financial relief programs and unemployment benefits. In fact, this is precisely how the attacks on Government of Canada services happened.
In August, Canada Revenue Agency (CRA) was forced to temporarily shut down after three separate breaches compromised the personal data of 5,500 Canadians. Attacks used logins and passwords collected from previous hacks of accounts worldwide. Once the attackers got through, they changed the banking information and email addresses on thousands of accounts to claim or redirect CERB payments. Overall, a total of 11,200 accounts for the Government of Canada services were compromised, including over 9000 “GCKey” accounts used to access various online portals.
COVID-19 has also opened up new avenues of attack for identity thieves, including door-to-door solicitations and phone scams where callers pose as contact tracers to pry payment or other banking information from unsuspecting victims—information real contact tracers would never ask for. Fraudsters may even rifle through your trash for any confidential personal and/or work-related documents that would normally be disposed of in a corporate shredder.
How have digital response measures to COVID-19 increased cyber risks?
In March of 2020, companies reacted swiftly to shift office workers home with minimal disruption to operations. Digital response measures, like remote work, personal device usage, and cloud services, were implemented with speed and scale to maintain public safety and business continuity. But in their haste, many organizations embraced these solutions without the foresight or consideration for security that would normally go into new service deployment. Ultimately, the fast-tracked adoption of technology has both inadvertently created new cyber risks and aggravated existing gaps in protection.


Remote Work
With millions working from home, many for the first time, remote work has become a major security concern. Some of the main issues include:
-
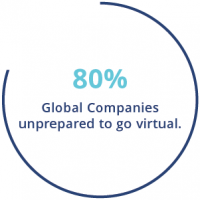
Lack of Preparation: Over 80% of global companies admitted they were unprepared to go virtual so abruptly. Only 53% of global remote workers received clear instructions or awareness training. 16% received no clear communication at all.
-
Strained IT Infrastructures: Globally, the top tech challenges encountered by corporate IT teams last year included: instructing employees, securing remote workers, and strengthening protections on third-party apps needed for telework. For these reasons, IT staff are still struggling, nearly a year later, to iron out security patches created by the initial transition.
-
Weak Home Security: Home networks are typically set up with cheap, easily hackable equipment, rather than secure firewalls, encryption, and modems, making them clear targets for cybercriminals.
-
Public Wi-Fi: Many are taking advantage of work-from-home arrangements and cheap hotel rates to either travel and work on-the-go or escape their homes during the workday. But using unencrypted connections, like hotel or public Wi-Fi, allows hackers to sneakily distribute malware, infiltrate accounts, and intercept corporate data.
RELATED: The Top 6 Remote Work Security Concerns.
Personal Devices
At the start of the pandemic, many organizations were forced to rely on employees’ personal devices for business functions, either temporarily until new equipment arrived, or on a permanent basis if it wasn’t financially feasible to purchase new materials. Currently, while two-thirds of Canadian employees say they’re using company-issued equipment, half of them also report regularly working on their personal devices.
Despite the recent rise of corporate Bring-Your-Own-Device (BYOD) policies, personal computers, smartphones, and other mobile devices have long been considered a weak link in the cybersecurity chain. Here’s why:
-
More Entry Points: Inside business networks, data and devices are protected. But with 90% of the world’s office professionals working from home, the concept of a security perimeter has quickly become outdated. Cybercriminals’ digital entry points have increased exponentially, with routine exposure to corporate systems through domestic PCs, laptops, and routers.
-
Poor Security: Employers can do little to shield unmonitored, personally-owned, consumer-grade equipment. Additionally, weak password practices, infrequent security updates, and little management control over software downloads can give attackers a new vector to gain foothold. And if any client data is leaked, the organization, not the employee, will still be held liable, even if the breach occurred on a personal device.
Cloud Computing
Given the urgency for flexible, scalable, off-premises technology services, cloud computing has played a crucial role in adapting businesses to the new landscape. In fact, cloud adoption rates have never been higher, with cloud spending reaching $29 billion in the first quarter of 2020; this is a 37% rise over the same period in 2019. Simultaneously, there was a 630% jump in threat events targeting cloud services between January and April 2020.
Why? Businesses’ sudden and rapid shift to cloud hosting, often without the advice of in-house security personnel or proper due diligence, may have caused them to overlook risks like:
-
Misconfigurations: Hasty adoption can increase the likelihood of cloud misconfigurations, such as mismanaged permissions, lack of audit or governing controls, firewall issues, and more. Misconfigured servers prevent computing assets from functioning properly and expose data to threat actors, accounting for 19% of all malicious attacks according to IBM Security.
-
Security Blind Spots: Cloud services are delivered by organizations known as Cloud Service Providers (CSPs), who retain direct control over all aspects of security and privacy. Businesses have little to no visibility into CSPs’ internal protections, which means they likely won’t be able to resolve, or even identify, any cloud misconfigurations until it’s too late.
Human Error
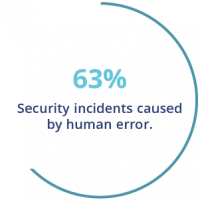
COVID-19 aside, human error is still the biggest risk factor when it comes to cyber threat. Cyber claims data from Willis Towers Watson shows that 63% of security incidents in 2020 were caused directly by employees, be it through accidental disclosure, data loss, or a spoofing scam. During this time, employees may be even more susceptible to scams due to:
-
Lack of Focus: Given the circumstances and public thirst for information, cybersecurity isn’t exactly top of mind for everyone. Workers might be more anxious, distracted, and thus, likely to ignore unusual site activity, divulge their login credentials, or fall for a phishing attack. Terranova Security’s 2020 Phishing Benchmark Global Report revealed that close to 20% of employees were quick to click on phishing email links, a spike from 11% in 2019.
-
Lack of Oversight: Out of sight, out of mind. Time and distance away from the office and nearby technical support may have weakened employees’ general sense of cyber vigilance. They may be more careless or more inclined to ignore IT policies, reuse passwords, and save confidential data off the VPN.
-
Lack of Training: You don’t know what you don’t know. Many employees might be simply unaware of how to handle sensitive data—particularly if they’re using a personal device or newly installed company software—recognize the signs of a scam, or report a privacy breach.
What’s on the horizon?
The effects of the virus will be with us for quite some time, long after the pandemic is over. It is impossible to tell how COVID-19 will unfold and how that will affect the global cyber landscape, but for now, we can anticipate the following:
COVID-19 will continue to be a catalyst for digital transformation.
Much of the groundwork for digital solutions and e-commerce were already in place due to a growing technological shift that was well underway before the pandemic. However, COVID-19 has accelerated this transition to a point of no return. Both businesses and clients are seeing the convenience and the rewards of going virtual.
Despite the increased risks, remote work is here to stay—and not just until the crisis is over.
Calls for workplace flexibility have been building for decades. Post-pandemic, employees and employers alike will be looking to work-from-home, or possibly work-from-anywhere, more frequently. As remote work becomes the new normal, senior leaders may even be open to hiring-from-anywhere. Organizations will need to be equipped to accommodate long periods of remote working and distributed workforces.
Cyberattacks will become more sophisticated, difficult to detect, and costly.
So far, we know that having a remote workforce has been found to raise the average total cost of a data breach by nearly $137,000, for an adjusted average total cost of $4 million. But cybercriminals show no signs of slowing down. And they’re getting craftier than ever by adapting as new opportunities arise. As more organizations expand their digital presence, we will continue to see a steady and aggressive influx of cyberattacks.
2021 will be all about DDoS and formjacking.
2020 was the year of phishing. And while it remains a pressing concern, DDoS and formjacking attacks will pick up speed since more transactions are happening online. Moreover, with online sales forecasted to reach the trillions in 2021 and the launch of 5G networks, increased connectivity is likely to widen attack surfaces across all industries.
Ransomware attacks will increase, but businesses won’t be able to keep up with demands.
More and more victims are paying up, with few, if any, repercussions for illicit behaviour. In 2018, only 39% paid their attackers. By 2020, that figure was estimated to be as high as 58%, with global damages from ransomware attacks projected to reach $20 billion by 2021. As attackers’ appetites grow, payments may no longer be a viable option.
Insurance companies may pull back on ransomware coverage.
Ransomware attacks are growing in frequency and severity, with higher-than-expected damages among businesses. As a result, insurance carriers are incurring huge losses and Cyber Insurance premiums are going up. To protect their existing clients and ensure they’re financially secure enough to cover future security claims, insurers might start to be more cautious about what cyber risks they can take on. Eventually, carriers may have no choice but to either: remove ransomware coverage completely, or make it optional, but with a heavy premium and deductible.
To ward off the threat of ransomware, it is imperative for all businesses to bolster their cyber hygiene and invest in preventative security measures. Although standalone Cyber Insurance policies are still available to cover expenses in the event of a privacy breach, a strong risk management approach is critical to supplement organizations’ existing coverage and ensure maximum protection.
To learn more about how insurance rates fluctuate—and why—read our report: The Insurance Pendulum: What’s a Hard Market?
Businesses will continue to suffer harsh breach consequences.
Experts can all agree: the industry response doesn’t match the current cyber landscape. Many organizations are still underestimating the effects of cyberattack and ignoring gaping holes in cybersecurity. And without adequate protections, most SMBs won’t be able to survive the fallout of even a minor breach, which could expose businesses to federal penalties, prolonged litigation, and severe reputational harm.
Privacy laws will get stricter and businesses will struggle to maintain compliance.
Canadian businesses are beginning to show signs of compliance fatigue. Only 36% notified a regulatory body of a breach in 2020—down from 58% in 2019—and only 44% informed their customers. This level of non-compliance doesn’t bode well for the proposed changes to privacy law, in which Bill C-11, or the Digital Charter Implementation Act, 2020 (DCIA) would replace PIPEDA with the Consumer Privacy Protection Act (CPPA). If enacted, the CPPA would introduce more stringent regulations, akin to the EU’s GDPR, to give consumers greater control and transparency over their data. Organizations would be required to implement a privacy management program, obtain informed consent prior to data collection, and pay steep penalties of up to $25 million for compliance violations. In comparison, fines under PIPEDA are currently capped at $100,000.
What can businesses do?
Given the global conditions, companies facing dire financial straits may be tempted to lessen their protections, reduce their insurance coverage, and cut down on any seemingly unnecessary expenses. But in this day and age, security is a required cost of doing business. Organizations cannot afford to let down their cybersecurity guards, especially since public advice encourages consumers to restrict purchases to large shops with more extensive protections, rather than SMBs or smaller e-commerce websites that may be more prone to breach.
As we move into 2021, now is the time for companies to embrace the future of work as digital, revisit their cyber strategies, and adopt a more proactively vigilant posture for the year ahead. Prevention is the first line of defence.
We recommend a three-pronged risk management approach that emphasises security, education, and insurance, with key considerations highlighted below.
Security
-
Update: Tighten your security patches. Ensure that any response measures deployed early on are now robust and enterprise-grade. Invest in privacy compliance.
-
Support: Provide IT teams with the support and resources they need to address cyber risks.
-
Adapt: Tailor your security protocols to your organizations, the cyber landscape, and any emerging risks.
-
Plan: Develop or amend your incident response and business continuity plans in case of a breach.
RELATED: COVID-19: How to Keep Employees Cyber-Safe While Working From Home.
Education
-
Train: Provide specific security awareness training to teach employees: how to handle sensitive data; how to use software; what threats your organization faces; how to identify those threats; and how to recognize signs of a breach. Consider high-quality training courses and automated phishing simulations.
-
Communicate: Keep employees updated about risks as they crop up, where they can go for help, and how to report security incidents.
-
Encourage: Work towards a cyber risk-aware culture. Find ways to meaningfully engage workers and offer incentives or rewards for doing so.
Insurance
Do not neglect the importance of cyber-specific coverage. If your business suffers a breach, your general liability policies won’t protect you—they’re not specifically designed to address cyber risk. But a dedicated Data Security & Privacy Breach Insurance policy can respond quickly and effectively to help you offset some of the potential financial loss from legal fees, damages, and associated expenses.
Your plan may also include:
-
Access to a forensic investigations team to help you determine the size and scope of the breach;
-
A breach coach who will guide you through the legal process of navigating a breach under attorney-client privilege. The coach will tell you what to report and when;
-
Funds to set up credit monitoring and notification for affected parties; and
-
A team of public relations consultants to help manage your organization’s reputation;
-
And more.
How can we support you?
As cyber risks evolve, we must evolve how we approach risk. With over 40 years of experience and a specialized knowledge of cyber markets, PROLINK is ahead of industry trends. We will help you become resilient in the face of attack while you focus on managing your people, your clients, and business. Our dedicated team of risk advisors will:
-
Conduct a robust assessment of your existing insurance policy to detect any coverage gaps;
-
Identify cyber perils, attack scenarios, and any potential losses based on your unique operations and risks;
-
Share what steps others in your industry are taking and advise you accordingly;
-
Determine the scope of responsibilities for all incident management team members;
-
Deliver you a specialized solution, tailor-made for a new era of cyber risk with clearly defined parameters of coverage.
To learn more about your exposures—and how you can protect yourself—connect with PROLINK today.
PROLINK’s blog posts are general in nature. They do not take into account your personal objectives or financial situation and are not a substitute for professional advice. The specific terms of your policy will always apply. We bear no responsibility for the accuracy, legality, or timeliness of any external content.